While checking personal spam emails that I received today, my interest was drawn by a certain email claiming that users can get $2400 by downloading the casino application:
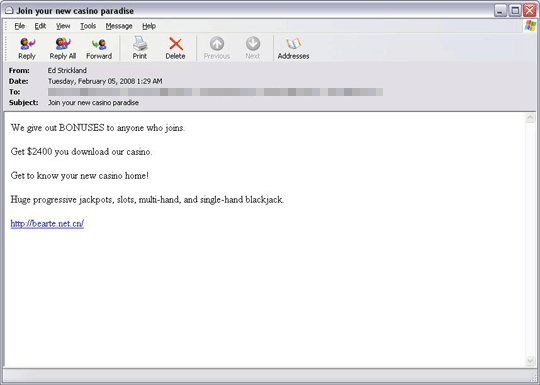
Once you click on the link hxxp://bearte.net.cn, you are sent to this Web page:

This Web page asks you to download a file named InstallCasinoV2.exe. The said file is already under analysis; more updates to follow.
But this is not what I really want to talk about here. This casino story made me think about pay-per-install programs and I decided to look for those programs with a simple search as follows:

As you can see, I couldn’t have made it any simpler.
Here is the result displayed:

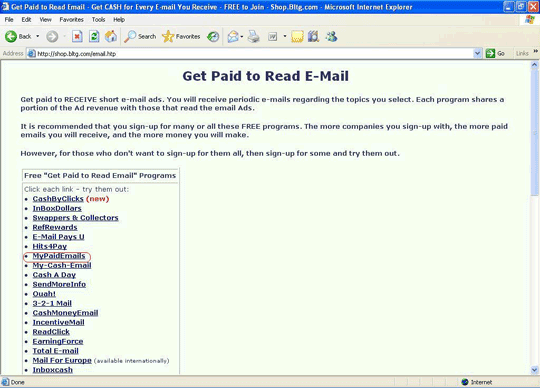
The second link here is interesting: “Get Paid to Read Email”. I thought, why not, so I clicked on this link and this is what it led to:
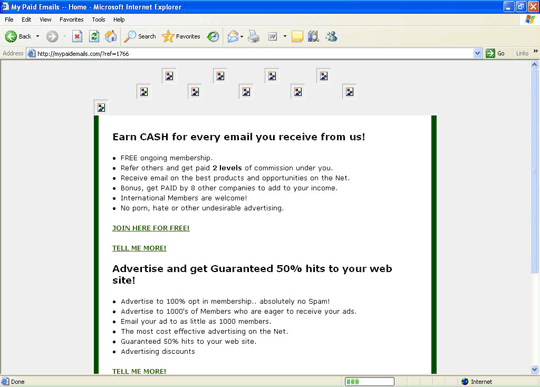
This page looked every bit normal, and I started to browse and check the links on the left. So I just clicked on the link “MyPaidEmails”. It proved to be the beginning of a huge infection chain.
Once the following page is loaded, you have no more access to your computer, which becomes too busy loading iFrames, scripts and malware:
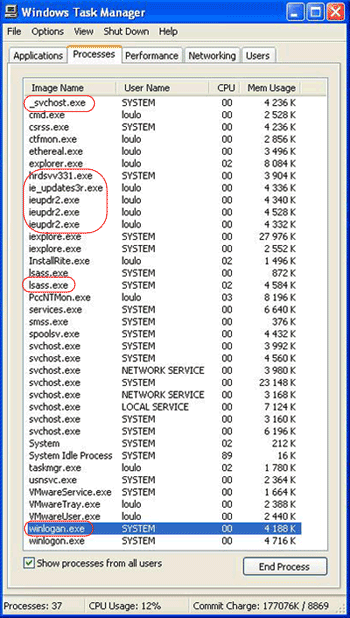
You can see the number of malicious processes loaded in memory from the screenshot of the machine’s Task Manager above, and this is only the beginning of the infection. All the files gathered are already under analysis, as well as the URLs added for Web Threat Protection (WTP) blocking. The malicious files are detected as the following:

Once you click on the link hxxp://bearte.net.cn, you are sent to this Web page:

This Web page asks you to download a file named InstallCasinoV2.exe. The said file is already under analysis; more updates to follow.
But this is not what I really want to talk about here. This casino story made me think about pay-per-install programs and I decided to look for those programs with a simple search as follows:

As you can see, I couldn’t have made it any simpler.
Here is the result displayed:

The second link here is interesting: “Get Paid to Read Email”. I thought, why not, so I clicked on this link and this is what it led to:

This page looked every bit normal, and I started to browse and check the links on the left. So I just clicked on the link “MyPaidEmails”. It proved to be the beginning of a huge infection chain.
Once the following page is loaded, you have no more access to your computer, which becomes too busy loading iFrames, scripts and malware:


You can see the number of malicious processes loaded in memory from the screenshot of the machine’s Task Manager above, and this is only the beginning of the infection. All the files gathered are already under analysis, as well as the URLs added for Web Threat Protection (WTP) blocking. The malicious files are detected as the following:
- TROJ_DLOADER.BG
- TROJ_DLOADER.CO
- TROJ_NUWAR.KE
- TROJ_PROXY.KN
- TROJ_DLOADER.DJA
- TROJ_DLOADER.DJH
- TROJ_PAKES.XH
- TSPY_LDPINCH.AJW
- TSPY_LDPINCH.AOL
- HTML_AGENT.HDF
- HTML_AGENT.HFA
- HTML_AGENT.HDU
- HTML_AGENT.HEC
- HTML_AGENT.HEL
- HTML_AGENT.HFB
- HTML_AGENT.HFC



Comment